SSL and TLS Explained: Protecting Online Communication
Updated on : 10 December, 2024, 10:30 AM IST

Image Source: Proton
Table Of Contents
- 1. What Are SSL and TLS?
- 2. Key Features of SSL and TLS
- 3. Why Are SSL and TLS Important?
- 4. How SSL and TLS Work
- 5. Similarities Between SSL and TLS
- 6. Differences Between SSL and TLS
- 7. The Evolution of SSL/TLS
- 8. The Role of SSL/TLS Certificates
- 9. How to Implement SSL/TLS on Your Website
- 10. Common Misconceptions About SSL and TLS
- 11. Troubleshooting Common Issues
- 12. Future Trends in SSL/TLS
- 13. Conclusion
Table Of Contents
In today's digital landscape, the security of online communication is paramount. As cyber threats continue to evolve, the need for robust encryption protocols has never been more critical. This is where SSL (Secure Sockets Layer) and TLS (Transport Layer Security) come into play.
What Are SSL and TLS?

Image Source: Linkedin
SSL (Secure Sockets Layer) is a cryptographic protocol developed by Netscape in the mid-1990s to secure internet communications. It provides a secure channel between two devices operating over the internet or an internal network. SSL has undergone several iterations, with SSL 3.0 being the last version before it was succeeded by TLS.
TLS (Transport Layer Security) is the successor to SSL, introduced in 1999 as an update to SSL 3.0. While TLS retains many of SSL's features, it offers enhanced security measures and improved performance. Today, when people refer to SSL, they often mean both SSL and TLS collectively, but it is essential to note that TLS is the protocol currently in use.
Key Features of SSL and TLS
Both SSL and TLS offer the following key features:
-
Encryption: Converts data into unreadable text to prevent unauthorized access.
-
Authentication: Confirms the server’s identity using SSL/TLS certificates.
-
Data Integrity: Ensures that data isn’t altered during transmission.
-
Session Resumption: TLS allows faster reconnection for returning clients, improving performance.
Why Are SSL and TLS Important?
When you browse the internet, your data (like login credentials or credit card numbers) travels between your device and a website's server. Without SSL/TLS, this information is transmitted in plain text, making it vulnerable to interception by hackers. SSL and TLS protect your data by:
-
Encrypting Information: Data is scrambled into an unreadable format that only the intended recipient can decode.
-
Ensuring Data Integrity: They prevent data from being altered during transmission.
-
Authenticating Websites: They verify the identity of websites to ensure you’re communicating with a legitimate server, not an imposter. SSL and TLS are the foundation of HTTPS (HyperText Transfer Protocol Secure), which you see in your browser’s address bar. HTTPS signals that the website you’re visiting is secure.
How SSL and TLS Work
The process of establishing a secure connection using SSL/TLS involves several key steps known as the SSL/TLS handshake. This handshake allows the client (typically a web browser) and server to agree on encryption methods and establish a secure session.
The Handshake Process
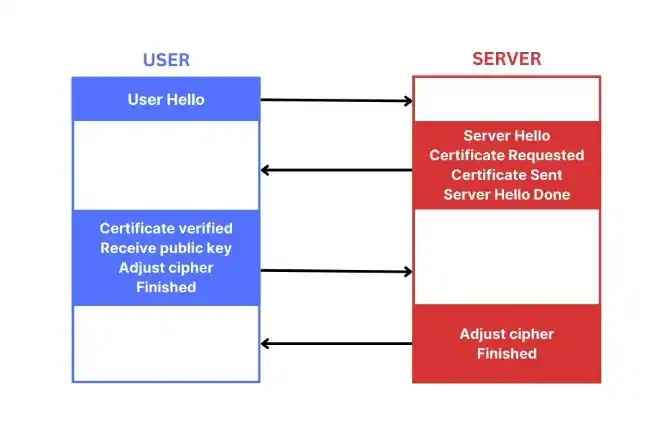
Image Source: Redswitches
-
Client Hello: The client initiates the handshake by sending a "hello" message to the server, which includes supported SSL/TLS versions, cipher suites (encryption algorithms), and a randomly generated number.
-
Server Hello: The server responds with its own "hello" message, selecting a cipher suite from the client's list and sending its digital certificate containing its public key.
-
Certificate Verification: The client verifies the server's certificate against trusted Certificate Authorities (CAs) to ensure its validity.
-
Session Key Creation: If the certificate is valid, the client generates a symmetric session key, encrypts it with the server's public key, and sends it to the server.
-
Secure Connection Established: The server decrypts the session key using its private key. Both parties now use this session key for symmetric encryption during their communication.
Encryption Mechanisms
SSL/TLS employs both asymmetric and symmetric encryption:
- Asymmetric Encryption: Used during the handshake process to securely exchange keys. It involves a pair of keys: a public key (shared openly) and a private key (kept secret). Only the corresponding private key can decrypt data encrypted with the public key.
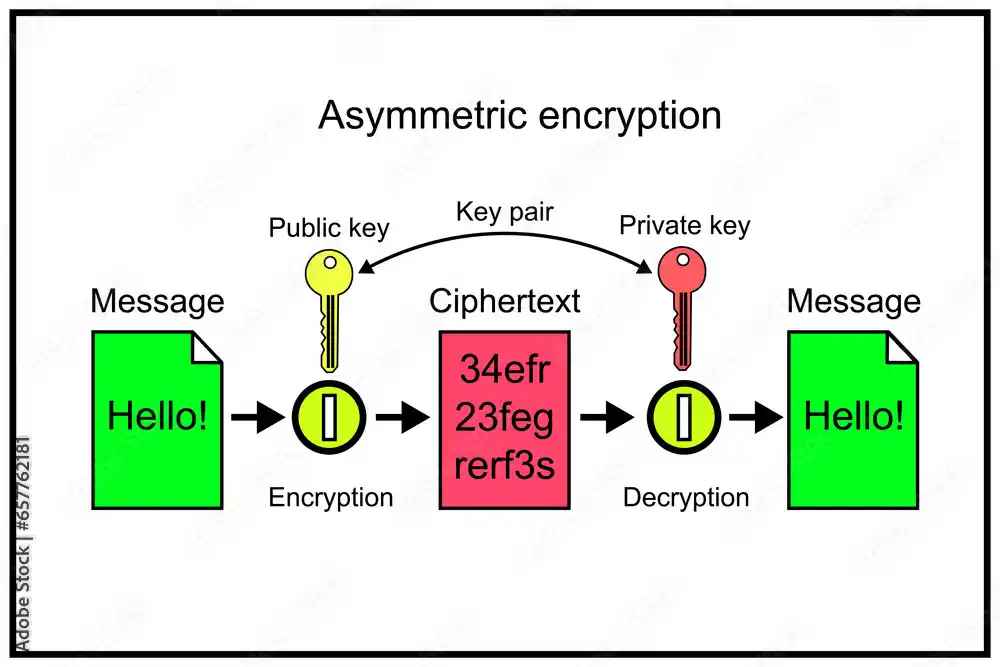
Image Source: Adobe Stock
- Symmetric Encryption: Used for encrypting data during an active session once both parties have established a shared session key. Symmetric encryption is faster than asymmetric encryption and is used for transmitting bulk data securely.
Similarities Between SSL and TLS
SSL and TLS share several key features:
-
Encryption: Both encrypt data to protect it from being intercepted.
-
Authentication: Both verify the server’s identity using certificates.
-
Integrity: Both ensure data isn’t tampered with during transmission.
-
Usage: Both are used for securing websites, emails, file transfers, and other types of communication.
Differences Between SSL and TLS
While SSL and TLS serve similar functions, there are notable differences between them:
| Feature | SSL | TLS |
|---|---|---|
| Version | Older protocol | Updated protocol |
| Security | Contains known vulnerabilities | Enhanced security features |
| Cipher Suites | Limited | Broader range of options |
| Handshake Process | Simpler | More complex |
| Performance | Slower | Improved performance |
The Evolution of SSL/TLS
-
SSL 1.0: Never released due to security issues.
-
SSL 2.0: Released in 1995 but quickly found to be insecure.
-
SSL 3.0: Introduced in 1996 but now obsolete due to vulnerabilities.
-
TLS 1.0: Launched in 1999 as an improved version of SSL 3.0.
-
TLS 1.1 and 1.2: Introduced stronger encryption and better performance.
-
TLS 1.3: Released in 2018 with even better security and efficiency.
Most modern websites use TLS 1.2 or TLS 1.3
The Role of SSL/TLS Certificates
Image Source: Globalsign
An SSL/TLS certificate is a digital document that authenticates a website's identity and enables encrypted connections between web servers and browsers. These certificates serve three primary functions:
-
Encryption: They ensure that all data passed between web servers and browsers remains private.
-
Authentication: They verify that a website is legitimate, preventing impersonation.
-
Trust: They foster trust with users by indicating that their connection is secure through visible indicators like padlock icons in browsers.
How to Implement SSL/TLS on Your Website
If you’re a website owner, here’s how you can secure your site with SSL/TLS:
-
Purchase a Certificate: Get one from a trusted Certificate Authority (or use a free option like Let’s Encrypt).
-
Install the Certificate: Follow your web hosting provider’s instructions.
-
Update URLs: Change all website links from "http://" to "https://".
-
Test Your Website: Use online tools like SSL Labs to ensure everything is working correctly.
Common Misconceptions About SSL and TLS
- “SSL is the same as TLS.”
While they serve the same purpose, TLS is the updated version of SSL with better security.
- “If a website has HTTPS, it uses SSL.”
HTTPS (HyperText Transfer Protocol Secure) means the website is using encryption, but it’s usually TLS, not SSL.
- “SSL/TLS is only for websites.”
Besides websites, SSL/TLS secures email (SMTP, IMAP, POP3), file transfers (FTP), video calls, and even some apps.
Troubleshooting Common Issues
While implementing SSL/TLS can significantly enhance security, issues may arise that require troubleshooting:
Certificate Errors
Common errors include:
-
Expired Certificate: Ensure certificates are renewed on time.
-
Untrusted Certificate Authority: Verify that your CA is recognized by major browsers.
Mixed Content Warnings
- This occurs when some resources on an HTTPS page are loaded over HTTP instead of HTTPS:
- Fix this by ensuring all resources (images, scripts) are served securely over HTTPS.
Connection Issues
If users experience connection problems:
- Check server configurations for proper installation of certificates.
- Ensure firewalls or proxies aren’t blocking secure connections.
Future Trends in SSL/TLS
As technology evolves, so do security protocols:
- Adoption of TLS 1.3
The adoption rate of TLS 1.3 is increasing due to its simplicity and enhanced security features compared to previous versions.
- Post-Quantum Cryptography
With advancements in quantum computing posing potential threats to current cryptographic methods, research into post-quantum cryptography aims to develop new algorithms resistant to quantum attacks.
- Increased Focus on Certificate Transparency
Certificate Transparency initiatives aim to improve trust in certificates by making them publicly accessible for auditing purposes.
Conclusion
In summary, mastering SSL/TLS not only safeguards individual transactions but also fortifies the broader framework of internet security essential for modern communication—a crucial step toward creating a safer online environment for everyone. This expanded version provides additional depth on various aspects related to SSL/TLS while maintaining clarity on how they function as essential components of internet security today!


