OWASP Mobile Top 10 Uncovered: Real Breaches & Insights
Updated on : 03 April 2025

Image Source: google.com
Table Of Contents
- 1. Introduction to OWASP
- 2. M1: Improper Platform Usage
- 3. M2: Insecure Data Storage
- 4. M3: Insecure Communication
- 5. M4: Insecure Authentication
- 6. M5: Insufficient Cryptography Risks
- 7. M6: Insecure Authorization Risks
- 8. M7: Poor Code Quality Risks
- 9. M8: Code Tampering Risks
- 10. M9: Reverse Engineering Risk
- 11. M10: Extraneous Functionality Risk
- 12. Things to keep in Mind
- 13. FAQs
Table Of Contents
Introduction to OWASP
The Open Web Application Security Project (OWASP) is a globally recognised non-profit organization dedicated to improving software security. It provides free tools, documentation, and best practices to help developers and organizations identify, understand, and mitigate security risks in web and mobile applications.
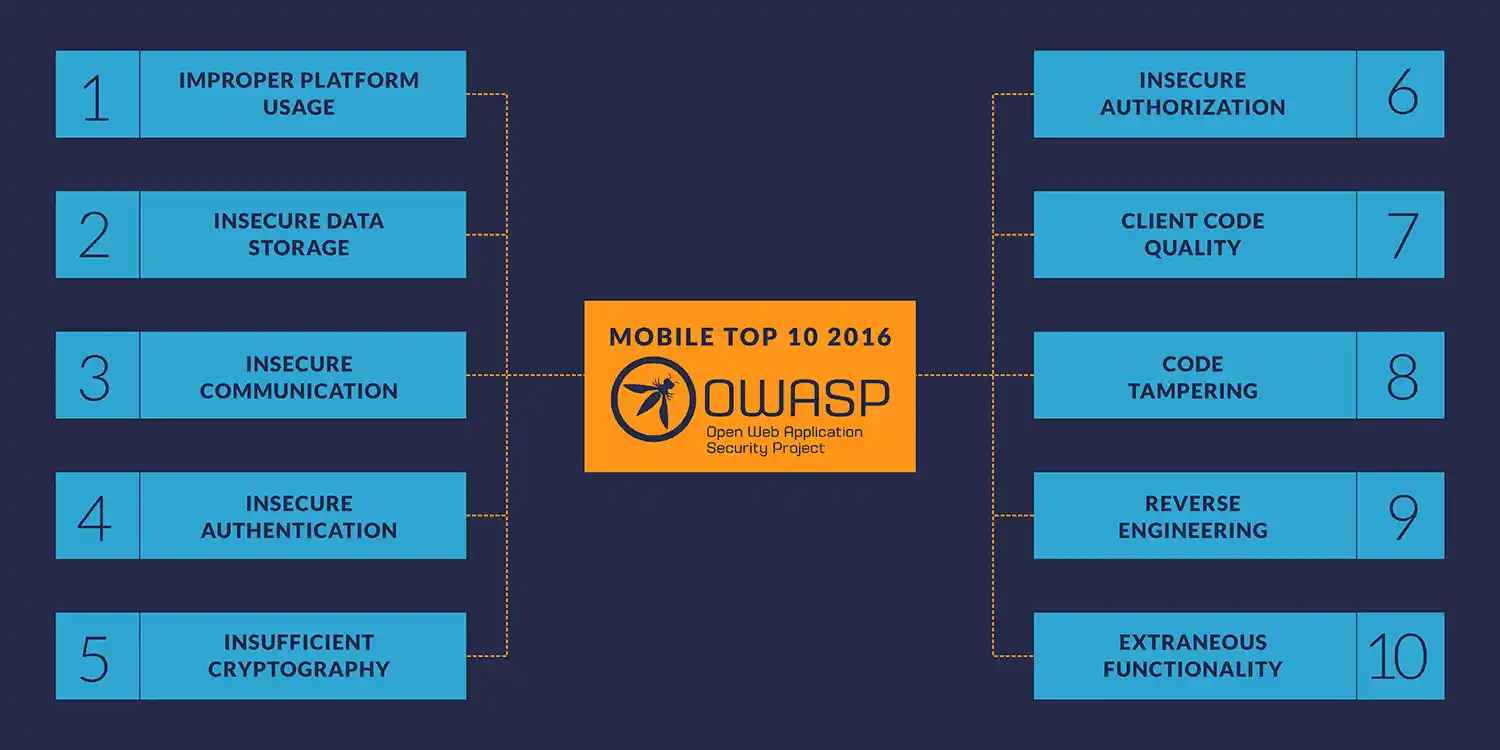
Image Source: AI-generated
M1: Improper Platform Usage
The Improper Platform Usage category in OWASP security testing refers to the misuse of device functionalities or the failure to implement platform security controls correctly. This can include improper handling of platform permissions, misuse of Android intents, and security flaws in biometric authentication methods like Touch ID and Keychain.
Real-World Case:
- In 2019, a vulnerability was discovered in Android's biometric authentication system, where some banking apps failed to properly validate fingerprint authentication.
- Attackers could bypass authentication by tricking the system into accepting unregistered fingerprints or using overlay attacks to intercept user credentials.
- This flaw allowed unauthorized access to sensitive financial information, putting users at significant risk.
Best Practices to Avoid Security Risk:
| Best Practice | Description |
|---|---|
| ✅ Ensure Secure Key Management | Do not allow Keychain encryption keys to be transmitted over insecure routes. Store keys on a single device to prevent unauthorized access on other servers or devices. |
| ✅ Implement Proper Access Control | Protect sensitive app data stored in Keychain by enforcing strict access control lists. |
| ✅ Restrict App Permissions | Request only essential permissions to limit unauthorized access and communication between applications. |
| ✅ Control Explicit Intents | Clearly define explicit intents to prevent unauthorized components from accessing sensitive information over the internet. |

AWS is Revolutionizing Mobile App Development with Scalable & Secure Solutions!
M2: Insecure Data Storage
The Insecure Data Storage category in OWASP security testing refers to the improper handling of sensitive user data, which can lead to unauthorized access, data breaches, and identity theft. This often occurs due to weak encryption, improper use of system storage, or failure to implement secure authentication mechanisms.
Real-World Case:
- In 2020, a security flaw in a popular mobile banking app exposed user credentials and transaction history.
- The app stored sensitive information, including account details and session tokens, in an unencrypted local database.
- Attackers who gained access to the device could extract this data, leading to fraudulent transactions and unauthorized account access.
Best Practices to Avoid Security Risks:
| Best Practice | Description |
|---|---|
| ✅ Encrypt Sensitive Data | Always encrypt sensitive user data at rest and in transit to prevent unauthorized access. |
| ✅ Use Secure Storage | Store critical data in secure storage solutions like Keychain (iOS) or Keystore (Android) instead of local databases or shared preferences. |
| ✅ Implement Strong Authentication | Ensure session tokens and credentials are protected with strong authentication and expiration policies. |
| ✅ Prevent Data Caching | Disable sensitive data caching in memory and logs to avoid accidental exposure. |
| ✅ Conduct Security Audits | Regularly test and audit data storage methods to identify vulnerabilities and strengthen security measures. |
M3: Insecure Communication
The Insecure Communication category in OWASP security testing refers to the failure to protect data transmitted between the mobile application, backend servers, and third-party services. Attackers can intercept unprotected data using man-in-the-middle (MITM) attacks, packet sniffing, or exploiting weak encryption protocols, leading to data leaks and unauthorized access.
Real-World Case:
- In 2019, a major healthcare app was found transmitting unencrypted patient data over HTTP instead of HTTPS.
- This exposed sensitive medical records, appointment details, and personal information to potential attackers monitoring network traffic.
- The flaw allowed unauthorized entities to steal confidential data, violating user privacy and regulatory compliance.
Best Practices to Avoid Security Risks:
| Best Practice | Description |
|---|---|
| ✅ Use HTTPS with TLS | Always enforce HTTPS with TLS 1.2 or higher to encrypt data during transmission. |
| ✅ Implement Certificate Pinning | Use certificate pinning to prevent MITM attacks by ensuring the app only communicates with trusted servers. |
| ✅ Avoid Hardcoded API Keys | Do not store API keys or secrets within the app code to prevent reverse engineering. |
| ✅ Validate SSL Certificates | Ensure proper SSL certificate validation to prevent attackers from using self-signed certificates. |
| ✅ Encrypt Sensitive Data | Encrypt any sensitive data before sending it over the network to add an extra layer of security. |
| ✅ Monitor Network Traffic | Regularly test for vulnerabilities using penetration testing tools to identify insecure communication channels. |
M4: Insecure Authentication

Image Source: AI-generated
The Insecure Authentication category in OWASP security testing refers to weaknesses in user authentication mechanisms that allow attackers to bypass login systems, steal credentials, or gain unauthorized access to user accounts. These flaws often arise due to weak password policies, improper session management, or missing multi-factor authentication (MFA).
Real-World Case:
- In 2021, a popular e-commerce app suffered a security breach when attackers exploited weak authentication mechanisms.
- The app allowed users to log in without verifying passwords properly, enabling attackers to take over accounts using credential stuffing techniques.
- As a result, users faced unauthorized purchases and personal data leaks.
Flawless, Secure, and Reliable Hexadecimal’s Mobile App Testing
Best Practices to Avoid Security Risks:
| Best Practice | Description |
|---|---|
| ✅ Enforce Strong Password Policies | Require complex passwords with a mix of uppercase, lowercase, numbers, and special characters. |
| ✅ Implement Multi-Factor Authentication (MFA) | Use MFA (e.g., OTPs, biometric authentication) to add an extra layer of security beyond just passwords. |
| ✅ Secure Session Management | Ensure session tokens are securely stored, expire after inactivity, and cannot be reused. |
| ✅ Prevent Brute Force Attacks | Implement rate-limiting and account lockout mechanisms to block repeated failed login attempts. |
| ✅ Encrypt User Credentials | Store passwords securely using strong hashing algorithms like bcrypt or Argon2. |
| ✅ Monitor Authentication Logs | Continuously track login attempts and alert users of suspicious activities. |
M5: Insufficient Cryptography Risks
The Insufficient Cryptography category in OWASP security testing refers to the use of weak or improperly implemented encryption algorithms that fail to protect sensitive data. This can lead to data breaches, unauthorized access, and exposure of critical user information. Attackers can exploit weak encryption to decrypt sensitive data, tamper with stored information, or perform cryptographic attacks.
Real-World Case:
- In 2020, a fitness tracking app suffered a data breach when it was discovered that user health data, including location history and activity logs, was encrypted using outdated and weak algorithms.
- Attackers were able to decrypt the data easily, leading to privacy violations and security concerns.
Best Practices to Avoid Security Risks:
| Best Practice | Description |
|---|---|
| ✅ Use Strong Encryption Algorithms | Always use industry-standard encryption algorithms like AES-256 for data at rest and TLS 1.2+ for data in transit. |
| ✅ Implement Proper Key Management | Store encryption keys securely using hardware security modules (HSMs) or secure key vaults. |
| ✅ Avoid Hardcoded Keys | Do not embed encryption keys in the application code to prevent reverse engineering. |
| ✅ Perform Regular Cryptographic Audits | Regularly review and update encryption implementations to mitigate evolving threats. |
| ✅ Use Secure Hashing for Passwords | Hash passwords using strong algorithms like bcrypt, PBKDF2, or Argon2 instead of weak hashes like MD5 or SHA-1. |
| ✅ Prevent Cryptographic Failures | Ensure proper padding, nonce generation, and randomness to avoid predictable encryption patterns. |

Want to Elevate Your Mobile App with Advanced Solutions?
M6: Insecure Authorization Risks
The Insecure Authorization category in OWASP security testing refers to flaws in access control mechanisms that allow attackers to gain unauthorized access to restricted resources. These vulnerabilities often arise from improper role-based access control (RBAC), broken authorization logic, or insufficient validation of user permissions.
Real-World Case:
- In 2021, a ride-sharing app faced a major security issue where users could manipulate API requests to access other riders' trip details.
- Due to improper authorization checks, attackers could modify the user ID in API calls and retrieve personal data of other customers, leading to privacy breaches.
Best Practices to Avoid Security Risks:
| Best Practice | Description |
|---|---|
| ✅ Implement Role-Based Access Control (RBAC) | Restrict access to sensitive resources based on user roles and privileges. |
| ✅ Validate Authorization for Every Request | Ensure every API request is validated against user permissions before granting access. |
| ✅ Prevent IDOR (Insecure Direct Object References) | Do not expose direct object identifiers (e.g., user IDs) in client-side requests without proper validation. |
| ✅ Enforce Least Privilege Principle | Grant users only the minimum permissions necessary for their tasks to reduce security risks. |
| ✅ Secure API Endpoints | Use authentication tokens and access control lists to prevent unauthorized API access. |
| ✅ Monitor and Audit Access Logs | Continuously track and log user activities to detect unauthorized access attempts. |
M7: Poor Code Quality Risks
The Poor Code Quality category in OWASP security testing refers to insecure coding practices that introduce vulnerabilities such as injection flaws, buffer overflows, and memory leaks. Poorly written code can lead to performance issues, security risks, and exploitation by attackers.
Real-World Case:
- In 2019, a social media platform experienced a major security flaw due to improper input validation.
- Attackers exploited a poorly sanitized user input field to execute SQL injection attacks, gaining unauthorized access to user accounts and personal data.
- This incident highlighted the importance of secure coding practices.
Best Practices to Avoid Security Risks:
| Best Practice | Description |
|---|---|
| ✅ Enforce Secure Coding Standards | Follow industry best practices and OWASP Secure Coding Guidelines to write robust and secure code. |
| ✅ Implement Proper Input Validation | Sanitize and validate all user inputs to prevent injection attacks (SQL, XSS, etc.). |
| ✅ Use Static and Dynamic Code Analysis | Regularly analyze code with security tools to detect vulnerabilities early. |
| ✅ Prevent Hardcoded Secrets | Avoid storing API keys, credentials, and sensitive information directly in the code. |
| ✅ Adopt Secure Error Handling | Ensure that errors do not expose sensitive information that attackers can exploit. |
| ✅ Conduct Regular Code Reviews | Perform peer reviews and security audits to identify and fix insecure code patterns. |
M8: Code Tampering Risks
The Code Tampering category in OWASP security testing refers to unauthorized modifications of a mobile application’s code or binary. Attackers can reverse-engineer, modify, or inject malicious code into an app to bypass security controls, steal sensitive data, or execute unauthorized actions.
Real-World Case:
- In 2020, a banking app was targeted by attackers who modified its APK file to remove security checks and inject malware.
- The tampered version was distributed through third-party app stores, tricking users into installing it.
- This led to credential theft and unauthorized transactions.
Best Practices to Avoid Security Risks:
| Best Practice | Description |
|---|---|
| ✅ Use Code Obfuscation | Apply code obfuscation techniques to make reverse engineering more difficult. |
| ✅ Implement Integrity Checks | Use cryptographic hashing to verify app integrity and detect tampering. |
| ✅ Enable Runtime Protections | Deploy runtime checks to identify unauthorized modifications while the app is running. |
| ✅ Secure App Distribution | Distribute apps only through trusted sources like Google Play and the Apple App Store. |
| ✅ Prevent Debugging and Hooking | Disable debugging in production builds and use anti-hooking techniques to prevent runtime modifications. |
| ✅ Monitor for Repackaged Apps | Continuously scan for unauthorized versions of your app to detect potential threats. |
M9: Reverse Engineering Risk

Image Source: Reverse Engineering Risk
The Reverse Engineering category in OWASP security testing refers to the process where attackers analyze an application's code to extract sensitive information, discover vulnerabilities, and modify the app’s behavior. This can lead to intellectual property theft, security bypasses, and unauthorized access to critical functionalities.
Real-World Case:
- In 2021, a mobile payment app was reverse-engineered by attackers, exposing encryption keys embedded in the source code.
- This allowed them to decrypt and manipulate financial transactions, leading to fraudulent activities and financial losses for users.
Best Practices to Avoid Security Risks:
| Best Practice | Description |
|---|---|
| ✅ Use Code Obfuscation | Apply code obfuscation techniques to make it difficult for attackers to analyze and understand the app’s code. |
| ✅ Remove Debugging Symbols | Strip debugging symbols and metadata from production builds to prevent attackers from extracting useful information. |
| ✅ Implement Anti-Tampering Mechanisms | Use runtime checks to detect modifications and prevent execution if tampering is detected. |
| ✅ Encrypt Sensitive Data | Avoid storing sensitive information in plain text and use strong encryption methods to protect critical data. |
| ✅ Disable Debugging in Production | Prevent attackers from using debugging tools to inspect and modify app behavior. |
| ✅ Monitor for Reverse Engineering Attempts | Use security monitoring tools to detect unauthorized access and potential reverse engineering threats. |
M10: Extraneous Functionality Risk
The Extraneous Functionality category in OWASP security testing refers to hidden or unnecessary features left in an application that could be exploited by attackers. These may include backdoors, debug endpoints, or admin functionalities that were meant for development but were not removed before production.
Real-World Case:
- In 2022, a retail app was found to have an exposed admin panel that was unintentionally left accessible in the production version.
- Attackers discovered this functionality and were able to modify product prices, issue fake discounts, and access customer data.
Best Practices to Avoid Security Risks:
| Best Practice | Description |
|---|---|
| ✅ Remove Debug and Test Code | Ensure all debugging tools, test endpoints, and developer features are removed before deploying the app. |
| ✅ Restrict Admin Functionalities | Limit access to admin features and ensure they are properly authenticated and authorized. |
| ✅ Conduct Security Reviews | Regularly review the codebase for hidden or unnecessary functionalities that could be exploited. |
| ✅ Use Feature Flags | Implement feature flags to control access to certain functionalities and disable unused features in production. |
| ✅ Perform API Endpoint Audits | Ensure API endpoints do not expose unnecessary internal functionalities or debugging logs. |
| ✅ Monitor Application Behavior | Continuously monitor for unusual behavior that may indicate the presence of extraneous functionality being exploited. |
Things to keep in Mind
1. Secure Data Storage – Encrypt sensitive data and avoid storing credentials in plain text.
2. Secure Communication – Use HTTPS with TLS, certificate pinning, and proper encryption for data transmission.
3. Strong Authentication & Authorization – Implement MFA, strong password policies, and proper access controls.
4. Secure Coding Practices – Validate all inputs, prevent injection attacks, and remove hardcoded secrets.
5. Proper Cryptography – Use strong encryption algorithms, secure key management, and avoid outdated cryptographic methods.
6. Code Protection – Use obfuscation, anti-tampering techniques, and prevent debugging or reverse engineering.
7. Remove Unnecessary Features – Eliminate debug code, hidden admin functionalities, and test endpoints before release.
8. Monitor & Audit – Regularly test, log, and analyze application behavior to detect security threats early.
FAQs
Q.1. Why is mobile app security important?
A: To protect user data, prevent breaches, and ensure privacy.
Q.2. How can I protect user data?
A: Use encryption, secure storage, and HTTPS for communication.
Q.3. How to prevent reverse engineering?
A: Apply code obfuscation, disable debugging, and use integrity checks.
Q.4. How do I secure API communication?
A: Use HTTPS, certificate pinning, and authentication tokens.
Q.5. How to prevent unauthorized access?
A: Implement MFA, strong passwords, and session management.
Q.6. What are common mobile app vulnerabilities?
A: Insecure data storage, weak authentication, unprotected APIs, and reverse engineering.
Q.7. How to ensure app security before launch?
A: Conduct security testing, code reviews, and follow best practices.


